When you work with critical assets in an operational technology environment, it is essential to monitor their performance. At the same time, you need to make sure that your critical assets are protected from any external threats.
However, connecting your OT environment with your IT network can cause vulnerabilities, as the connectivity exposes OT systems to cyber threats that can manipulate or disrupt critical operations.
Our DataDiode solves this issue by ensuring a unidirectional data flow at the highest security level. By blocking any data from moving into your OT environment via reverse data paths, you can prevent any external threats from entering the OT network. This way, your organization can safeguard the OT environment while allowing secure data transmission to your IT environment.
The challenge
Operational technology systems control and monitor physical processes in industrial operations, including utilities, manufacturing, and critical infrastructure. These systems are increasingly connected to IT networks and the internet to improve efficiency and data accessibility.
The key challenge lies in securely transmitting data from OT networks to IT networks without introducing vulnerabilities. Traditional firewalls, once the primary defense, are increasingly inadequate against sophisticated unknown vulnerabilities, often exposing the OT network to potential risks instead of protecting it.
The solution
Rather than relying on traditional firewalls, the hardware-enforced DataDiode ensures a unidirectional data flow. This way, you can safely transfer your OT data into your IT platforms, without the risk of unwanted reverse data transfers.
How it works
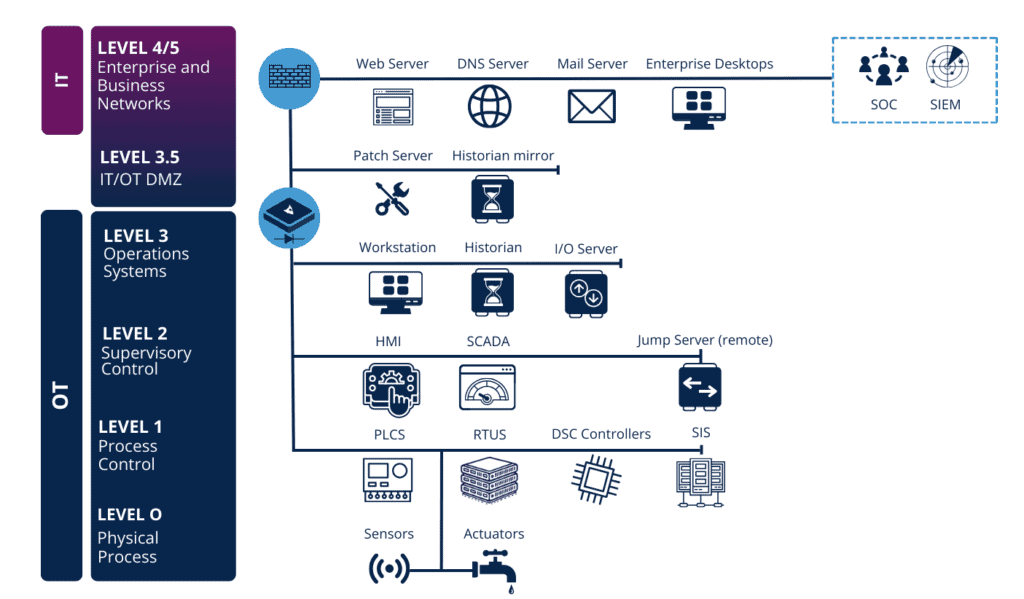
- Identify critical OT assets that require protection and map the data flows to and from these systems.
- Integrate the DataDiode into the existing network infrastructure, ensuring it connects the OT environment to the IT network securely.
- Monitor the outbound data flow to ensure operational integrity and that critical data reaches the IT network.
- Regularly audit the setup to ensure the DataDiode remains effective in isolating the OT environment from potential threats.
The benefits
- Secure, real-time monitoring: the DataDiode allows continuous, secure data flow to IT systems for effective monitoring.
- Operational continuity: the DataDiode protects the integrity of the OT network, ensuring that critical systems remain unaffected, available and operational.
- Compliance with regulations: The DataDiode meets stringent security requirements for critical infrastructure protection.

