Connection security is essential to protect classified information. Public organizations are prone to espionage, manipulation of data, and other cyber crimes. By ensuring a safe exchange of information, we can protect the Netherlands against current and future threats.
The safe exchange of information requires a high-quality cryptographic solution, made in the Netherlands. Our SkyTale Generation 3 Solution ensures the secure communication of classified information over untrusted networks.


The SkyTale product family consists of a range of IP network encryptors for the secure communication of classified information over untrusted networks, supported by an actively maintained roadmap.
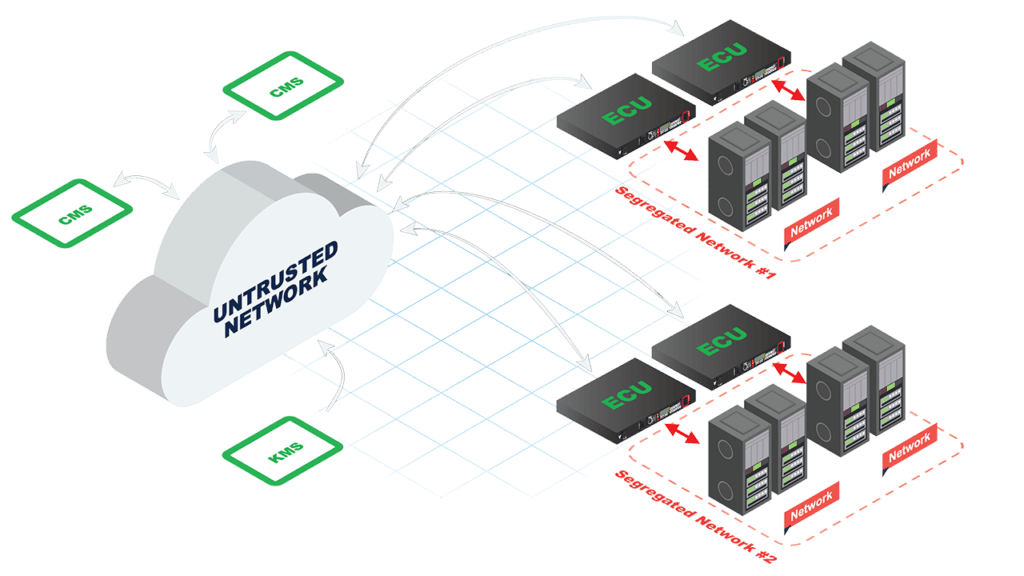
Each solution deployment consists of multiple systems:
The station that generates the keys used to encrypt the sensitive data.
Consisting of one or more CMS nodes. The nodes automatically distribute the key material from the KMS and load the configuration and key material into the ECU. The CMS is also used to diagnose and resolve problems.
A 19-inch 1U rack server providing encryption and decryption of the sensitive data.

In the defence sector, safeguarding classified information is critical to national security. Military organizations are constantly exposed to cyber threats, including espionage, data manipulation, and cyber warfare. Ensuring the secure exchange of sensitive information is essential to protecting military operations from both current and emerging threats.
Ensuring the secure exchange of sensitive information is essential to protecting military operations from both current and emerging threats.

Government institutions handle vast amounts of sensitive and classified information daily, from policy decisions to citizen data. The security of this information is crucial to maintaining national stability and public trust.
However, these organizations are frequent targets of cyber threats, including espionage, data breaches, and digital manipulation.

We explain everything you want to know about our network security solutions.

We assess your needs and requirements to come up with a high-level solution design that works for you.
We define, propose and support a PoC for you to test and use the solution in real life, in order to make sure your definition of success is met.

With all the information gathered above, we will be able to provide you with a tailored proposal for a fully operational solution at scale, including all required deployment and support services.
We help you implement the solution and customize it to fit your needs.
We are with you every step of the way, providing you the service you need.

Over twenty years of experience
As a pioneer in high-assurance security solutions, Fox Crypto brings more than twenty years experience in protecting classified information and data.
Solutions
Customer cases
Contact
Public key codes
© Fox Crypto 2025. All rights reserved. | Privacy statement | Cookie statement | Terms and conditions | Proclaimer | Responsible disclosure