The Fox Splunk Replicator is a powerful tool designed to address the significant security concerns associated with centralizing data for analysis and monitoring. This solution enables organizations to implement network segmentation for Splunk environments. Unlike firewalls, that are prone to software vulnerabilities, the Fox Splunk Replicator employs a DataDiode device to guarantee one-way data transmission at the hardware level. It can serve as a vital part of an organization’s security strategy to align with the NIS2 Directive. Wesley de Kraker is Software Engineer at Fox Crypto. Working alongside a team of experienced software engineers, he focuses on creating new software solutions for the market. He’s giving his insights on the Fox Splunk Replicator, and why organizations should use it.
Mitigate your security risks
To grasp the impact of the Fox Splunk Replicator, it is essential to understand Splunk first. Wesley explains: “Splunk is a widely used software for log analysis, primarily for IT operations and security monitoring. Developed by Splunk Inc., it collects data from various network devices, such as routers, firewalls, and servers, into a central location known as the Splunk indexer. These devices, known as forwarders, send their data in real-time to the Splunk indexer, enabling the analysis of large data volumes and providing insights into system performance, security threats, and operational issues.”
Centralizing data in one location poses substantial security risks. Wesley continues: “The problem our clients are facing is that they are centralizing all of their data, which presents a significant security concern. The Splunk indexer becomes a prime target for attackers because it holds all the comprehensive information from all network devices. Moreover, some of our clients are even combining data from different segmented systems, introducing the risk of data leakage between those segmented networks.”
To mitigate these risks, Fox Crypto relies on their EAL7+ certified DataDiode. This hardware device ensures unidirectional data flow, allowing data to pass from the Splunk forwarder to the indexer while preventing any possibility of data leakage in the opposite direction. This means it remains secure from potential breaches.
Integrating Splunk with the DataDiode ecosystem
The Fox Splunk Replicator integrates Splunk software within the DataDiode ecosystem, supporting the transmission of the Splunk protocol over DataDiode hardware. This integration ensures the confidentiality of data by enabling one-way data flow from forwarders to the indexer. Wesley notes, “We have developed the Fox Splunk Replicator to basically integrate the Splunk software within the DataDiode ecosystem. It supports sending the Splunk protocol over the DataDiode hardware. This completes the data transmission from the forwarders to the indexer without compromising the confidentiality of the data.”
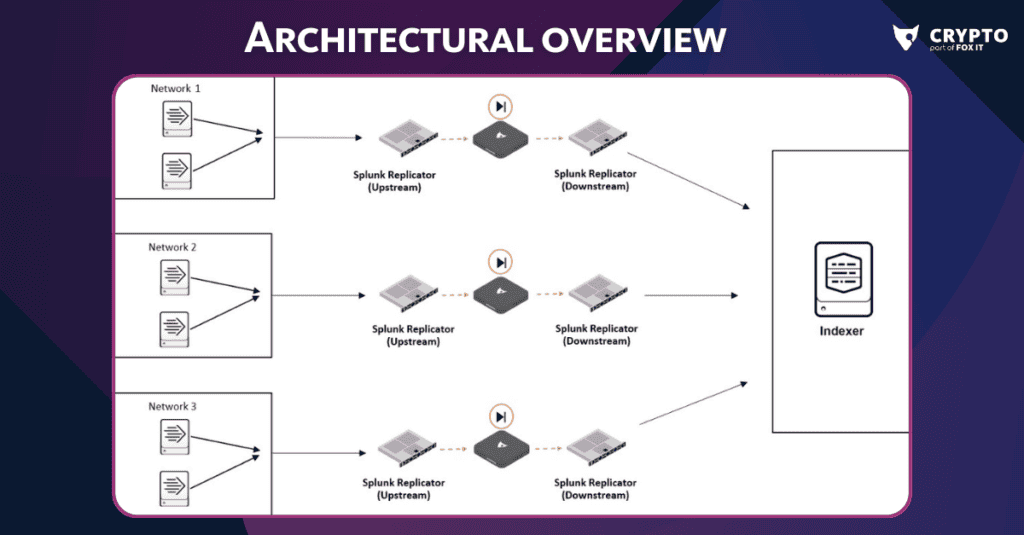
- The architecture of the Fox Splunk Replicator solution is shown in the figure above. Within each segmented network, forwarders collect data and send it to their respective upstream Splunk Replicator. From there, the data is transmitted through a dedicated DataDiode device, thus preventing any potential data leakage. The guarantee of data leak prevention assumes that all connections to the indexer are going through a DataDiode device, ensuring a unidirectional data flow as shown in the figure.
- Once the data passes through the DataDiode, it reaches the downstream Splunk Replicator, which then converts the one-directional data stream back into the original Splunk protocol. This data is finally delivered to the Splunk indexer for aggregation and analysis. For larger environments that require additional throughput and data filtering capabilities, a heavy forwarder can be integrated before the upstream Splunk Replicator. This heavy forwarder acts as an intermediary, capable of aggregating and filtering the data, thus reducing the load on the Splunk Replicator.
Key benefits of using DataDiodes in combination with Splunk
- Unidirectional data flow: DataDiodes enforce one-way data flow at the hardware level, making it physically impossible for data to flow back. This is a significant advantage over firewalls or other software solutions.
- High certification level: The EAL7+ certification of the DataDiodes corresponds to the highest security standards, ensuring robust protection for sensitive data.
- High performance: The Splunk Replicator supports transmission speeds of up to 8Gbps over a single DataDiode, making it suitable for clients with extensive performance requirements.
- Metadata integrity: The Splunk Replicator supports the Splunk-to-Splunk protocol over HTTPS, to maintain the integrity of metadata during transmission. This approach guarantees that all the valuable metadata, crucial for in-depth analysis, is preserved.
Overcoming development challenges
Developing the Fox Splunk Replicator presented significant challenges for the team, particularly in terms of performance. The solution needed to support high-speed data transmission to accommodate large environments. Wesley highlights: “The Fox Splunk Replicator stands out in the market because of two unique capabilities. The replicator can handle transmission speeds of up to 8Gbps over a single DataDiode, making it suitable for clients with extensive performance requirements. Moreover, other solutions often rely on the Syslog protocol. The problem with the Syslog protocol is that it strips away valuable metadata. Our replicator fully supports the Splunk-to-Splunk protocol over HTTPS. This ensures that all metadata, which is crucial for in-depth analysis, is also transmitted to the indexer.”
Compliant with regulatory requirements
The upcoming NIS2 Directive is an enhanced EU regulatory framework designed to strengthen cybersecurity across various sectors, expanding upon its predecessor to encompass a wider array of organizations. These organizations are mandated to perform risk assessments and adopt preventive measures to mitigate cybersecurity threats. In this context, the Fox Splunk Replicator can be a vital part of an organization’s preventive measures to align with the NIS2 Directive. It ensures a secure one-way data transfer from Splunk forwarders to indexers, thereby strengthening the organization’s cyber resilience.

