Contrary to common belief, DataDiodes are not merely intended for domain separation. According to Frans van Dorsselaer, Principal Architect at Fox Crypto, they are actually crucial for secure domain integration. Frans has spent years navigating the complexities of cybersecurity within Dutch government institutions. With extensive experience in developing secure communication solutions, he offers a fresh perspective on how DataDiodes are perceived and utilized. “We need to change the way we think about DataDiodes,” says Frans. “They’re not just barriers: they’re bridges that allow us to share information safely without compromising our networks.”
Misconceptions about DataDiodes and domain separation
DataDiodes are often misunderstood in cybersecurity. Many view them solely as tools for domain separation. This misconception leads to the underutilization of the true potential of DataDiodes. By only considering them as separators, organizations miss out on their ability to securely integrate domains, enabling controlled information sharing without risking network integrity. Frans adds: “A DataDiode is not just about separating domains: it’s about securely integrating them in a way that’s 100% safe.” He emphasizes that DataDiodes should be recognized for their role in secure domain integration. They allow selected and approved data to flow from one domain to another, while guaranteeing that no unauthorized data can enter or leave either domain.
“When you send information through a DataDiode, you’re keeping your entire database and information completely secure. You’re only sending out the information you’ve selected and approved. The confidentiality of the rest is guaranteed, and the outside world can’t influence you because nothing can come in.” This one-way flow creates a new, secure domain consisting of shared information that can be safely accessed by the receiving party without exposing the sender’s network to external threats.
Domain separation vs. domain integration
It’s essential to distinguish between domain separation and domain integration when discussing secure communication between different security domains, as each requires a unique set of solutions. The CIA principles of Confidentiality, Integrity, and Availability are critical to ensure the security of these communication channels.
Domain separation
In domain separation, there is no exchange of data between different security domains. The primary objective is to keep these domains isolated to prevent any potential security breaches that could occur through data transmission.
- Solution: VPNs like SINA, SkyTale, TCE, and PrimeLink are employed to protect the confidentiality and integrity of the data within a domain. These VPNs secure the communication channels, ensuring that data remains encrypted and inaccessible to unauthorized parties.
- Redundancy: Implementing redundancy measures protects the availability of the system, ensuring continuous operation even in the event of component failures.
Despite these measures, challenges such as physical protection of equipment, key management, configuration management, and the risk of covert channels still need to be addressed.
Frans explains: “In domain separation, you’re keeping domains completely isolated, and tools like VPNs ensure that. But isolation isn’t always practical or sufficient when data needs to flow between domains.”
Domain integration
Conversely, domain integration involves the exchange of data between different security domains. This is necessary when organizations need to share information securely across different networks or security levels.
Sending data to another security domain (export):
- Solution: A gateway often combined with a four-eyes release procedure, protects the confidentiality of the data being sent. This ensures that only authorized and verified information is transmitted to the external domain.
- DataDiode: Protects the integrity of the sending domain by preventing any external influences from affecting the system during data transmission.
Receiving data from another security domain (import):
- Solution: A DataDiode is used to protect the confidentiality of the receiving domain by ensuring one-way data flow. This prevents sensitive data within the domain from leaking out while allowing necessary information to come in.
- (Virus) scanners: These protect the integrity of the receiving domain by scanning incoming data for malware, viruses, or unauthorized code before it enters the network.
“When you need to integrate domains and exchange data, that’s where DataDiodes, gateways, and additional protections come into play,” Frans emphasizes. “It’s about allowing necessary communication without compromising the security of either domain.”
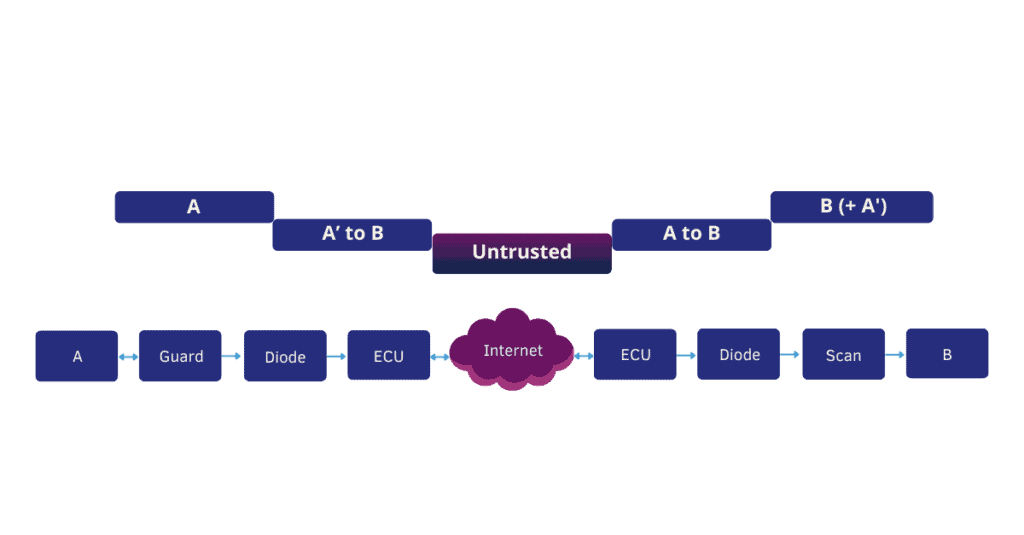
Figure explained:
The focus is on security domains. Security domains A and B are classified at a high level, while the shared “A’ to B” domain is classified at a lower level. The internet is unclassified (the lowest level). During export (on the left), you move from a high classification level to a lower one; during import (on the right), you move from a lower classification level to a higher one. As a result, domain B is ultimately supplemented with the partial information A’ from domain A.
To elaborate: for A (the sender), domain integration involves a Guard for confidentiality and a DataDiode for integrity. For B (the receiver), domain integration involves a DataDiode for confidentiality and a Scan for integrity. Since A and B are in different locations, they want to isolate their shared “A’ to B” domain from the internet through domain separation: a VPN connection provided by two End Cryptographic Units (ECUs).
Protecting confidentiality and integrity
“Confidentiality and integrity are two different products. Confidentiality and integrity both need to be protected at both ends of the communication, a total of four protection mechanisms. DataDiodes provide absolute security for one aspect —either confidentiality or integrity, depending on the direction of data flow— and software solutions are necessary for the other aspect but come with inherent vulnerabilities. For the sender, the DataDiode protects the integrity; for the receiver, the DataDiode protects the confidentiality. The DataDiode solves 100% of 50% of your problems. The other 50%—well, you’ll need something else for that, and that’s almost always software: a guard for the sender and a scanner for the receiver.”
The need for a collaborative approach
Frans van Dorsselaer’s insights shed light on the critical need for rethinking how Dutch ministries approach cybersecurity and secure information exchange. By viewing DataDiodes as domain integrators and adopting a layered security approach involving gateways, VPN boxes, and scrubbers, ministries can significantly enhance their security posture. However, achieving this requires strong leadership, coordination, and a willingness to collaborate across organizational boundaries.
The path forward lies in embracing a collaborative, strategic approach that leverages existing solutions, invests in interoperable technologies, and prioritizes national security over individual politics. With the right leadership and mindset, Dutch ministries can build a robust, integrated cybersecurity framework that protects the nation’s most sensitive information.

