The growing reliance on smartphones for both personal and business purposes has made smartphones prime targets for cybercriminals and state-sponsored actors. Mobile devices, especially smartphones, hold large amounts of sensitive information, making them a significant vulnerability for organizations. Jurjen Braakhekke, Product Manager at Fox Crypto, says: “We have to stop thinking of smartphones as just personal devices. They are data centers in our pockets, and that changes everything.”
However, despite their importance, secure mobile solutions are often not sufficiently controlled, particularly in sectors dealing with non-classified or low-classified information.
As mobile technology evolves and is integrated deeper into everyday business processes, the security of these devices has never been more critical.
The complexity of the mobile ecosystem, lack of security-by-design principles, and user behavior all contribute to significant risks, such as data breaches, espionage, and manipulation by malicious actors.
What tangible approaches are urgently needed to secure mobile solutions effectively?
Challenges in secure mobile communication
One of the key challenges in mobile security is the fragmentation of security measures across different sectors and organizations.
Securing mobile devices is far from straightforward due to factors such as:
- Application ecosystems: The diversity of apps and platforms complicates the implementation of uniform security protocols.
- Hardware vulnerabilities: Inherent weaknesses in device hardware can be exploited by malicious actors.
For many organizations, the focus on securing high-classified information (HGI) has overshadowed the need to protect non-classified and low-classified information (LGI), which still represents a significant target for cyber threats.
Secure mobile solutions for LGI domains are currently underdeveloped. The consensus is clear: more effective security measures must be implemented to safeguard this information. LGI and unclassified data often reside on mobile devices in far greater volumes than classified information, making those devices an attractive target for cybercriminals.
For instance, personal information or business communications processed on smartphones can be exploited for:
- Ransomware attacks: Locking users out of their data until a ransom is paid.
- Espionage: Criminals and state actors gaining unauthorized access to sensitive data.
Daniël Datau, Senior Business Development Manager at Fox Crypto, highlights this need for enhanced security, stating:
“There’s no such thing as too much security when it comes to mobile devices—especially when sensitive organizational data is at risk.”
Practical approaches to secure mobile solutions
To make mobile security more concrete and tangible, organizations need to adopt a layered approach that integrates technology, policy, and user behavior management. Key measures that can improve mobile security include:
- Enhanced security for low-classified information: Organizations must expand the scope of secure mobile solutions to cover LGI and unclassified data. Mobile security solutions for these domains are often overlooked but are critical in preventing unauthorized access and data leaks. For example, mobile device management (MDM) systems should be configured to create strict separations between personal and business use of mobile devices, thus ensuring data confidentiality.
- Hardware security enhancements: Commercial off-the-shelf (COTS) smartphones already provide hardware solutions that can enhance security, such as secure enclaves or trust zones within the device. These security measures help prevent unauthorized access to sensitive data. Furthermore, using technologies like hardware authentication allows organizations to verify that the device’s hardware hasn’t been tampered with, offering an extra layer of protection.
- Context-aware security policies: Security policies for mobile devices must be dynamic and context-aware. Rather than applying a one-size-fits-all approach, organizations should implement policies that vary depending on the role and access level of the user. A Zero Trust approach, for example, can consider factors such as location, network, and the security posture of the device to determine access rights to sensitive data.
- User awareness and behavior: A significant part of improving mobile security is fostering awareness and promoting safe user behavior. Many security breaches occur due to user negligence, such as sharing sensitive information via unsecured apps like WhatsApp. It’s essential to educate employees about the risks and ensure that they understand when and how to handle sensitive information securely.Daniël further emphasizes the proactive nature of mobile security, stating:
“The problem with smartphones is that people view them as personal, private devices. It’s something they own, so they’re less inclined to see them as part of their professional infrastructure. This disconnect between personal and work use is a major security risk, as sensitive information can easily be shared unknowingly.”
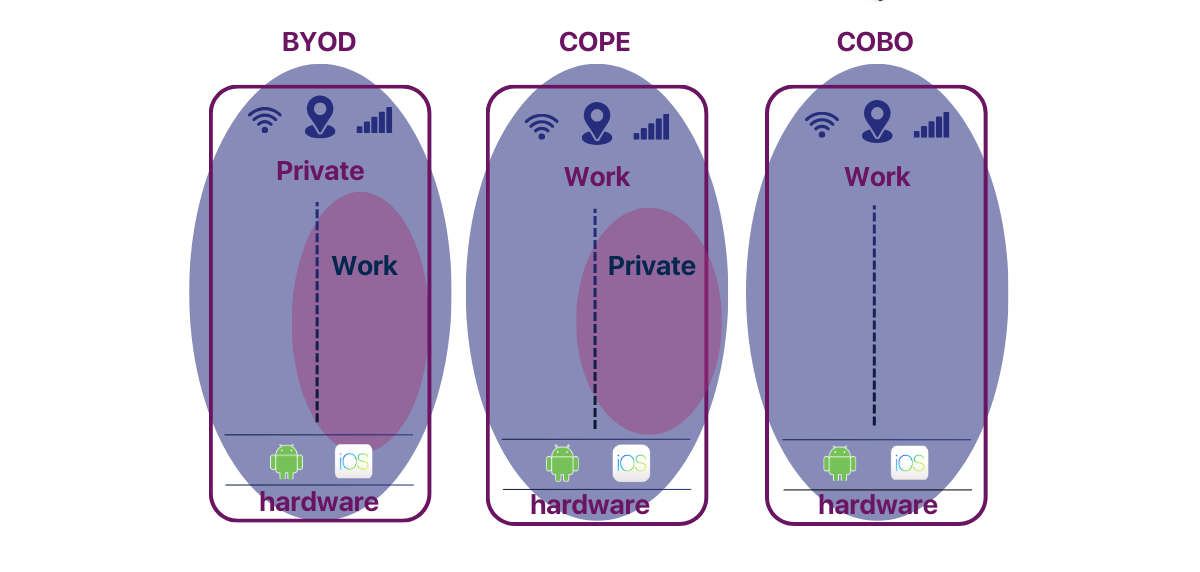
- Device configuration for security: Organizations can adopt several strategies for configuring devices based on their specific needs:
- A consumer device with a workspace offers freedom for the user but limits access to business data to a low-risk level.
- A business device with an unmonitored private space, allows greater organizational control over the hardware and security settings while restricting access to certain private apps.
- A business device with no private space, but some apps can run in isolated containers, maintain a boundary between personal and work data, though without any expectation of privacy.
- A fully business-controlled device, that only allows approved work-related apps.
Zero Trust approach and continuous monitoring
Zero trust is a security framework that assumes no user or device, inside or outside the network, can be trusted by default. Working on the basis of never trust, always verify, the framework enforces strict verification for every access request. Key principles of Zero Trust include:
- Least privilege: Granting users and devices only the access they need to perform their tasks.
- Continuous authentication: Verifying identities and devices continuously, rather than just at login.
- Network segmentation: Limiting the spread of potential breaches by isolating systems and data.
Applications of Zero Trust in unclassified/LGI domains
In the unclassified/LGI domain, organizations must implement Endpoint Detection and Response (EDR) solutions on smartphones and tablets.
This measure falls under the Zero Trust approach, as it strictly controls and manages access to corporate data, even on devices used for personal purposes. Continuous monitoring of both business and personal use is essential to prevent, detect, and respond directly to attacks and unintended data leaks with appropriate countermeasures. All business smartphones within an organization should at least have an Endpoint Protection app installed. This is effective against phishing, smishing, and can also detect and block malicious apps and websites.
Endpoint Detection Response (EDR) is mainly applicable when a problem has been detected. Zero Trust Network Access is an addition that applies dynamic policy and context-driven network authorization, authentication, and security to specific apps, the workspace, or even the entire device (see figure below). This reduces the attack surface. This is important because the traditional perimeter no longer exists due to the increasing use of cloud applications.
Conclusion: Moving toward tangible solutions
The need for concrete secure mobile solutions has never been more pressing. As mobile devices become increasingly integrated into business operations, the security of these devices must be a top priority. Jurjen adds: “If organizations don’t know how their mobile communication systems work, they can’t be aware of the risks that come with them.”
In many organizations, mobile security is insufficient. Organizations need to implement a more comprehensive, multi-layered approach to secure mobile communication. This includes investing in secure hardware, adopting context-aware security policies, and educating users on safe practices.
To make progress, public-private collaborations and the sharing of expertise are crucial. By working together, stakeholders from both the public and private sectors can develop effective solutions to secure mobile communications, ensuring that sensitive information remains protected in an increasingly mobile-first world.

