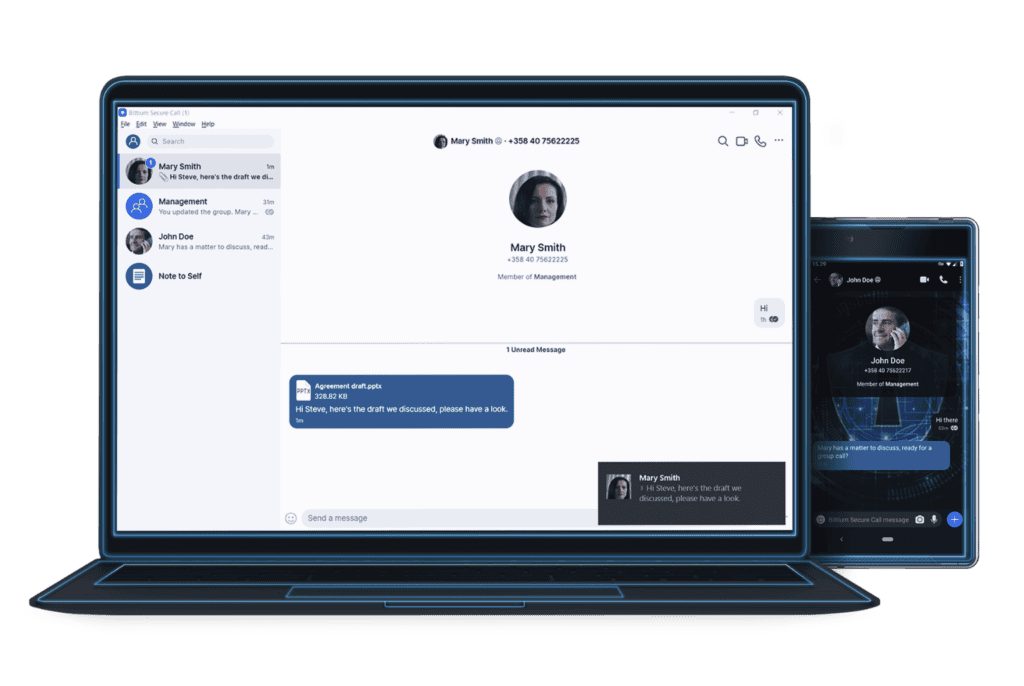
When you work with highly sensitive and confidential information, you need to be able to communicate in a way that meets the highest security requirements. We provide a certified, secure mobile communication solution for professionals that allows them to secure their data.


Hackers, cybercriminals, and state actors want to access large data flows that result from the use of smartphones. This way, they seek to obtain sensitive information with which they can identify, profile, and locate persons of interest. Our secure mobile solution provides a higher level of security than regular or burner phones. It allows users to wipe phones in an extremely fast and efficient manner.
The solution provides a flexible, user friendly and highly configurable Mobile Device Management solution. Our twelve-layered protection, which includes layers such as remote attestation, advanced anti-tamper technologies, and mandatory use of VPN, ensures your data is continuously protected.
Our secure mobile solution is built with multi-layered security, including secure boot with hardware and software integrity validation, tamper detection and non-rootable firmware.
The solution supports secure voice and messaging applications, ensuring encrypted and confidential communication, including Bittium SafeMove® VPN software.
The solution comes with extensive device management capabilities, allowing organizations to fully control and monitor the device fleet.
The solution includes a hardware-based privacy mode that can be activated with a dedicated button.
The solution supports multicontainers, which allow users to separate work and personal data securely.
Designed to withstand harsh conditions, the solution is resistant to dust, water, shock, and extreme temperatures.

Ensure civil servants who work in different locations abroad to set up secure connections to work on confidential documents and share status updates with colleagues in other locations.



We explain everything you want to know about our secure mobile solution.

We assess your needs and requirements to come up with a high-level solution design that works for you.
We define, propose and support a PoC for you to test and use the solution in real life, in order to make sure your definition of success is met.

With all the information gathered above, we will be able to provide you with a tailored proposal for a fully operational solution at scale, including all required deployment and support services.
We help you implement the solution and customize it to fit your needs.
We are with you every step of the way, providing you the service you need.

Over twenty years of experience
As a pioneer in high-assurance security solutions, Fox Crypto brings more than twenty years experience in protecting classified information and data.
Solutions
Customer cases
Contact
Public key codes
© Fox Crypto 2025. All rights reserved. | Privacy statement | Cookie statement | Terms and conditions | Proclaimer | Responsible disclosure