Every year, attacks grow in frequency and sophistication. World Economic Forum states: “Beyond AI, 2024 could see record-breaking data breaches. In 2023, the landscape of global data breaches significantly intensified from previous years, including a 72% increase in the number of data compromises over the previous high in 2022.” This situation demands that all organizations, but especially critical infrastructure and governments, make cybersecurity a top priority. The NIS2 legislation was set up exactly for that reason, and ISA-IEC 62443 provides even more depth. It defines critical infrastructure as a broad concept and requires organizations to protect themselves. In this article, we will explain the importance of cybersecurity and how the DataDiode fits in.
The rising stakes of cybersecurity
Gilles Loridon is a cybersecurity expert with 30 years of experience in IT and cybersecurity, and 25 years of knowledge in OT cybersecurity. He’s the CEO of Global Security Network (GSN), a company that has been delivering high-end Security projects in the Middle East since 2000. He explains why cybersecurity is critical, not only for companies, but for everyone: “After COVID everyone is relying on the digital world. Think about your train tickets, airplane tickets, groceries, electricity, and water bills – everything is digital. None of us receive paper bills anymore. That automatically means that cybersecurity is not optional anymore, but a necessity. Brick-and-mortar stores are closing down because everyone does their shopping online. Same goes for big supermarkets. There has been a massive shift to digitize every aspect of our lives. Of course that comes with an increase in cyberattacks. Especially critical infrastructure is constantly under attack.”
NIS2 Directive in critical infrastructure
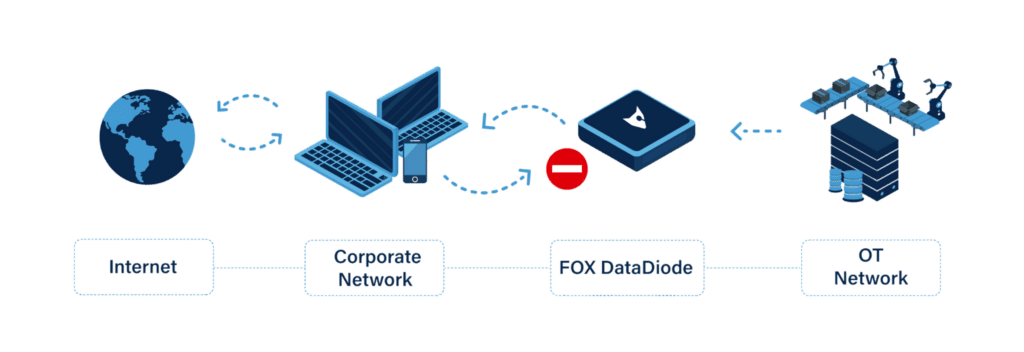
As Gilles emphasizes: critical infrastructure has long been a primary target for cybercriminals due to the high-impact consequences of successful attacks. In Europe, this reality has led to the creation of the NIS2 Directive—a critical piece of legislation aimed at improving the cybersecurity posture of vital infrastructure. NIS2 mandates that organizations strengthen their security practices and encourages segmentation to limit the impact of breaches. This is where DataDiodes play a crucial role. By enforcing one-way data traffic, DataDiodes align perfectly with NIS2’s goals, protecting your assets against external attacks and ensuring that vital operations remain protected, as shown in the image below:
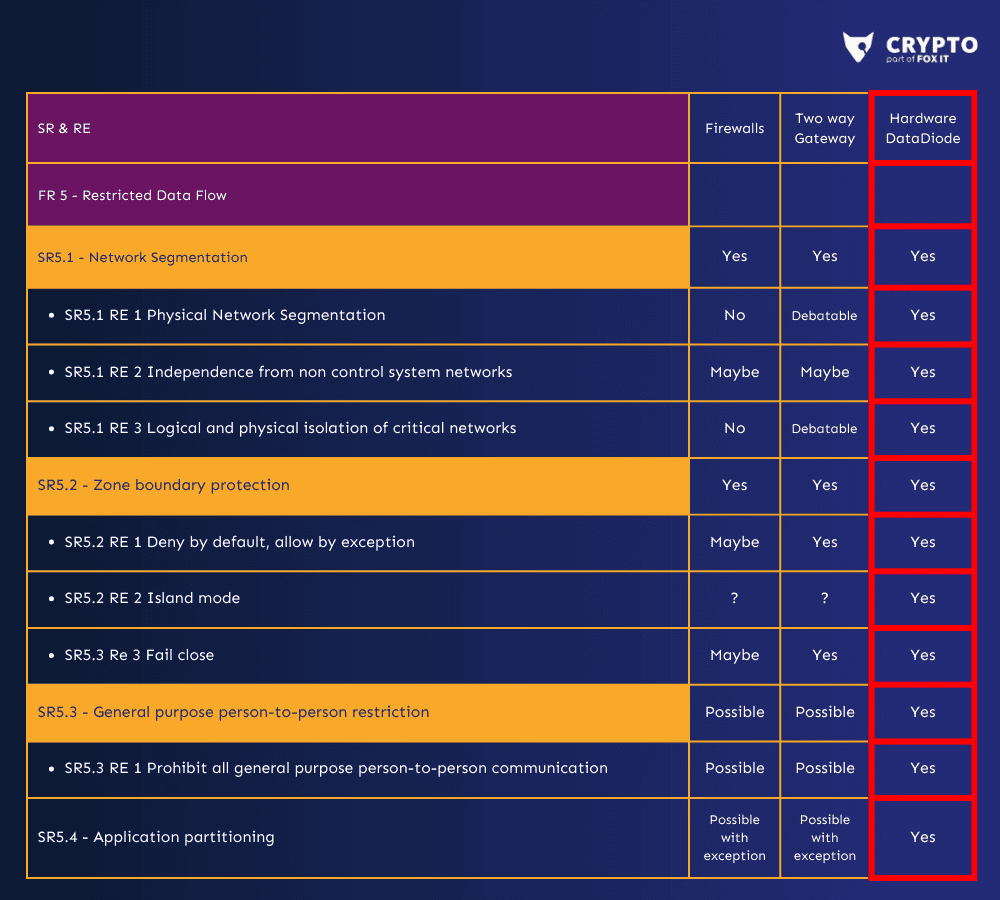
The need for increased segmentation based on risks is intensified by NIS2. ISA-IEC 62443 takes this a step further by providing a standard. When considering the OT market, ISA serves as a significant incentive for implementing more DataDiodes. Network segmentation and firewalls or virus scanners may not offer comprehensive protection. It’s crucial to recognize that ISA standards indicate firewalls alone aren’t sufficient for SL-4 security levels. In accordance with this legislation, the DataDiode emerges as the only effective solution, as you can see in the comparison chart below:
Evolving threats in cybersecurity
According to Gilles, cybersecurity threats have become worse in recent years. “We moved from relatively unprofessional to extremely professional cybercriminals. The amount of money currently generated by cybercrime places it among the foremost markets globally, probably bigger than the illegal drug trade. This naturally implies that cybercriminals are funded in large numbers, as they follow the money.”
Besides that, the cybersecurity landscape has seen a huge rise in Ransomware as a Service. Malicious code is rented out to cybercriminals who don’t have the technical skills to develop their own malware. This model has democratized access to ransomware, increasing the frequency and breadth of attacks globally. Also, the shift towards remote work has expanded the attack surfaces available to cyber criminals. With more employees working from home, often on less secure networks and devices, the potential entry points for attackers have multiplied. This shift has required a rethinking of network security strategies, with secure connections and other cybersecurity measures.
How to keep your organization safe
The rise of AI plays a huge part in cybersecurity. Important is to look at how you can protect your organization from these newly generated attacks. Gilles’ company GSN is using DataDiodes to protect its clients. They started implementing DataDiodes over 14 years ago, and now they’re industry specialists. They mainly focus on integrating DataDiodes for governments, but also for critical infrastructure, mostly in the energy sector.
The DataDiode plays a vital role
Gilles’ point of view regarding the latest developments in cybersecurity is the following: “Looking at AI, many people see this as a big threat in cybersecurity. AI can write excellent phishing emails, but to create an attack fully generated by AI, is something I don’t see happening. It’s not that difficult to recognize an attack, but sometimes we’re still not able to do it because of the nature of our connection to the internet. And that’s exactly where the DataDiode comes in. The DataDiode doesn’t depend on AI, or humans. And because DataDiodes cannot be hacked, it works, period. The OT/IT segementation market for critical infrastructure and companies in batch processing are perfect for the use of DataDiodes.”
DataDiodes are particularly crucial in environments where the highest standard of data security is required, such as military, government, and critical infrastructure sectors. By ensuring data can only travel in one direction, DataDiodes eliminate the risk of external attacks aimed at extracting sensitive information or causing problems on OT networks.
Future predictions
The role of DataDiodes is expected to become more prominent. Innovations in technology may lead to improved functionalities of DataDiodes. That means expanding their use beyond high-security sectors to more commercial environments, where data security is becoming increasingly vital.
Gilles predicts a significant shift in the demand for DataDiodes, foreseeing a future where a hybrid model—a blend between a traditional firewall and a DataDiode—becomes essential. He envisions this new variant as a cost-effective solution with a smaller size and footprint, making it suitable for new markets. He explains: “This innovation could safeguard critical components in transportation sectors such as trains, cars, and airplanes, which are currently vulnerable. I also see potential for two-way DataDiodes that combine the flexibility of firewalls with robust security to prevent unauthorized access. This way, the key vulnerabilities associated with current firewall technologies will be addressed for customer who can’t implement on-way security because of business logic constraints (typically in discrete manufacturing).
The power of the DataDiode is to be able to sleep at night. We know there’s no AI, no software, and no human intervention. A hacker can attack your IT, they can mess up your emails or your website, but they will not stop your production, because of the DataDiode.”

